

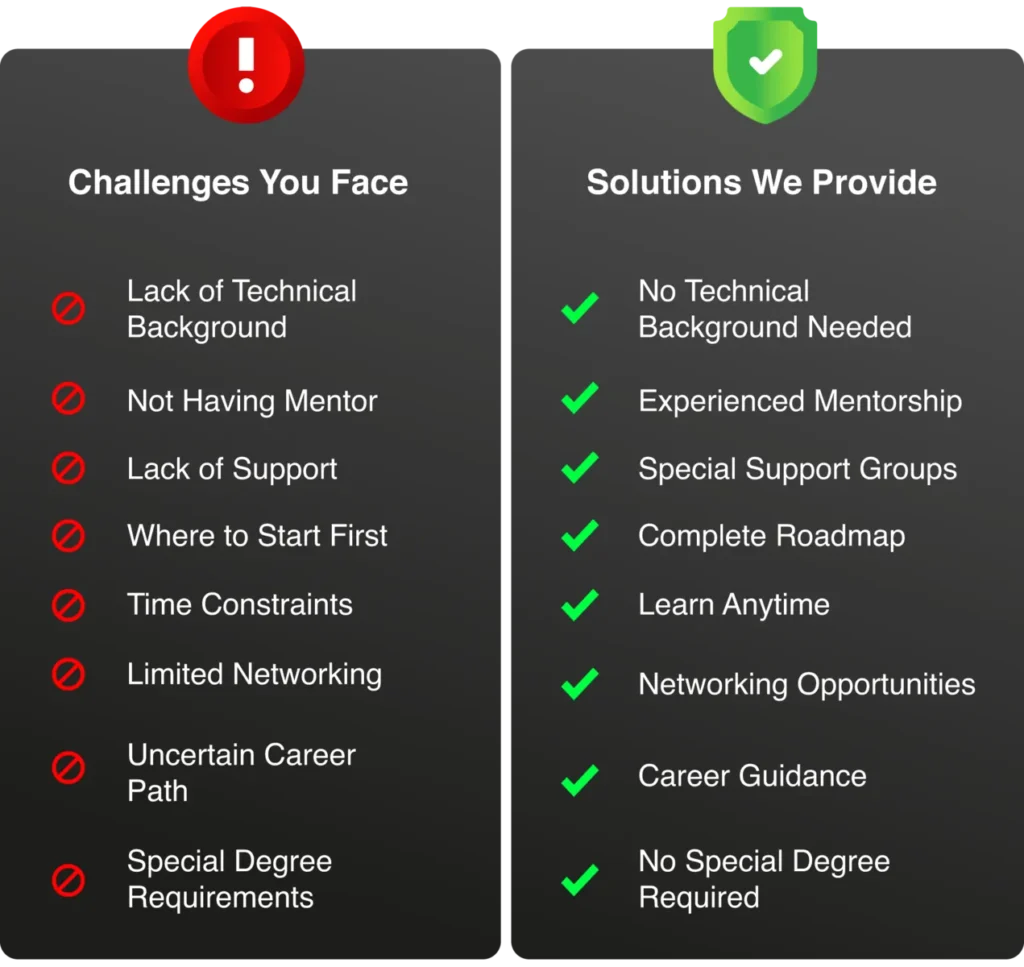
Latest Additions
Let AI Hack For You!
Get our brand new AI-powered hacking courses, absolutely free!
Complete lab Solution to Safely Practice Ethical Hacking Techniques.
Free certification upon course completion
(Applicable for Job)
Learn Ethical Hacking & Cyber Security To Make Career In Bug Bounty Hunting, Pentesting, Cyber Security Analyst. Now with Advanced Hacking with Artificial Intelligence
Even If Your Are Not From Computer Background
⭐⭐⭐⭐⭐ 4.9/5 (from 6,457+ students)
- 30+Practical Courses
- Up-To-Date 2025
- In Urdu Language
- Lab Solutions
- 100% Job Guarantee
- Free Certification
Expert Trainers
Our Ethical Hacking Full Course Is Led By An Expert Trainer Having Years Of Experience In The Field. All Topics Are Covered In-Depth And In An Easy-To-Learn Way.
Practical-Oriented
This Is A Practical-Oriented Course Where You Work On Essential Tools, Test Different Systems, Get Regular Assignments, And Practice The Skills You Learn.
Placement Assistance
We Have Partnerships With 100+ Companies To Assist You In Exploring Great Job Opportunities. You Will Find Tips And Help In The Interview Preparation.
Doubt Resolutions
You Can Ask Your Questions And Share Doubts, After Completing Lecture. All Your Doubts Will Be Resolved On Time & Efficiently To Ensure Quality Learning.
The online ethical hacking certification course by TutorNextGen helps you learn all aspects of ethical hacking from scratch. You don’t need to have any prior experience in cybersecurity to acquire these skills. This course covers all the concepts (from beginner to advanced), including computing networking attacks, enumeration, malware, ransomware, phishing, attack vectors, vulnerabilities, DoS/DDoS attacks, social engineering, footprinting, sniffing, and much more. You will get to work on tools and set up an ethical hacking lab for practice. Our ethical hacking online course also contains professional certification and job assistance, helping you to find high-paying career opportunities. You can become a Security Analyst, Cybersecurity Expert, Network Security Administrator, Cybersecurity Consultant, IT Security Manager, and work on several other roles.

- High Demand For Cybersecurity Experts
- Cybersecurity is evergreen industry
- Unlimited Career Growth opportunities
- Skills that no one knows
- Opportunities to work high profile agencies
- Work with Government officials
- Good salary package
- Create Awareness to people
GIFT FOR YOU
Limited Time Only
Master Android Hacking
with CRAX RAT
Latest Methods- Latest Tools- Latest Technology
Real-Time Device Control
Undetectable Payloads (FUD)
Advanced Post-Exploitation
Perfect for Beginners
Order Before 1ST March To Get These Offers
Free Access
Hacker GPT- AI for Hackers
Free Access
Let AI Hack for you
Free Access
Dark Web & Deep Web
Free Access
Password Cracking
Free Access
Advance Social Engineering
Free Access
Exploitation Course
Top 3 Pakistani Ethical Hackers
Course Features

Industrial Internship

Certification

Job Hunting Techniques

Self-Paced
Tools & Technologies Covered



















Claim Your Limited Time Offer Before It's Too Late:
WHO IS THIS FOR?
Beginner
If you are new to the field of cybersecurity and eager to build a solid foundation, our courses provide a comprehensive introduction to key concepts, tools, and techniques.
IT Professionals
If you are already working in the IT industry and wish to specialize in cybersecurity, our courses offer advanced training to enhance your existing skill set and expand your career opportunities.
Students and Graduates
If you are pursuing a degree or have recently graduated in a related field, our courses can supplement your academic knowledge with practical, industry-focused skills that employers value.
Security Enthusiasts
If you have a passion for cybersecurity and want to deepen your understanding, our courses provide in-depth insights, hands-on experiences, and advanced strategies to sharpen your expertise.
No matter your background or level of experience, our courses are designed to accommodate learners of all levels and help you progress in your cybersecurity journey.
Each month, you’ll be updated with new essential Tools to become a better version of yourself as a cybersecurity professional.
Demo Video
Watch the glimpse of the course before Buying – What you can do after Learning.
Contents of the Course:
17 sections • 130+ lectures • 21hour total length
Introduction
Virtual LAB Setup For Practicing At Home
• Download-and-install-virtualbox
• Install-Kali-Linux-On-Virtualbox-1
• Install-Metasploitable-2-On-Virtualbox
• Install-Windows-10-On-Virtualbox
• Virtual-Networking-Between-Virtual-Machines
Best Practice For Information Gathering [ActivePassive]
• Overview-And-Objective-Of-Information-Gathering
• Information-Gathering-By-Using-Search-Engine
• Information-Gathering-By-Using-Social-Sites
• Information-Gathering-About-Website
• Gather-Domain-Owners-Personal-Details-Whois
• Information-Gathering-About-Dns-And-Mail-Server
• Collecting-Emails-And-Gather-Information-From-Emails
Know More About Your Target-Scanning And Enumeratoin
• Overview-Of-Network-Scanning
• Scan-Network-For-Live-Hosts
• Scan-Hosts-In-Nework-Open-Ports
• Different-Techniques-Port-Scanning
• Enumeration Nmap ScriptEngine
• Detect-Service-Version-Os-Detail
• Nmap-Scan-Result-Output-Result
Google Hacking And Google Hacking Database
• Overview-Of-Google-Hacking
• Overview-Of-Google-Operators
• Overview-Of-Google-Hacking-Database
Windows Hacking And Security
• How to change Windows 10 password
• Change Windows Password By Backdoor
• Bypass Windows Login Screen
• Dump Windows 10 Password Hashes And Crack It
• Enable Syskey Password To Protect Windows-10
Linux Security And Hacking
• Linux User And Password Management
• Change Linux User Password In Single User Mode
• Implement Immutable Attribute And Protect Password Files
• Protect Grub Bootloader
• Remove Grub Bootloader Password Protection
• ump Linux Hashes
Password Cracking Techniques
• Overview Of Password Cracking And Types
• Creating Dictionary By Using Crunch
• Creating Dictionary Using Cwel
• Cracking Online Services
• Rule Based Dictionary Attack
• Zip Password Cracking With Bruteforce Attack
• Collect Username And Password Using Keylogger
Protect Your date From Hacking’s EYE
• Ntfs Data Stream In Action
• Detect Alternate Data Stream
• Overview Of Steganography
• Steganography In Action Quickstego
• Overview Of Encryption For Protecting Data
• Efs In Action And Backup Certificate
• Circumstances Of Losing Efs Data And Recovery
• Bitlocker And Bitlocker Go In Action
• Overview And Installation Of Veracrypt
• Veracrypt in Action
Trojan And Virus
• Overview Of Trojan
• Trojan Infection And Evading Techniques
• Trojan Detection Techniques
• Cports
• Driversview
• Jv-16-Registry
• Netstat
• Processmonitor
• Service Monitor
• Startup Monitor
• Tcpview
• Countermeasure From Trojan
Honeypot
• Overview And Types Of Honeypot
• Honeypot Kfsensor In Action
Proxy Server
• Overview Proxy Server
• Types Of Proxy Server
• Configure Proxy In Browsers
• Bounce Your Ip Like ProHacker Eps
• Elite Proxy Checker
• Metasploit Framework-All In One Hacking Console
• Getting Started
• Component Metasploit
• Authentication Bruteforcing Against Online Services
• Metasploit Gui Armitage
• Armitage One More Step
• Msfvenom Create Trojan For Windows
• Client Side Attack Linux Trojan
• Wireless Hacking – WPA WPA2 Encryption
• Enable WEP WiFi Router
• Cracking Wirerless Encryption – WEP
• Enable WPA In Wifi Router
• Cracking Wifi WPA/ WPA2 Encryption
Network Security And Hacking
• Basic Understanding Network Devices
• Mac Flooding Attack Against Switch In Network
• Arp Spoofing Attack In Lan
• Detect Arpspoofing Attack On Windows
• Mac Spoofing Attack In Windows And Linux
• Sniffing Get Username And Password From The Network
• Dhcp Starvation Attack
Social Engineering
• Overview of Social Engineering
• Types Of Social Engineering
• Types Of Social Engineering And Human Based Se
• Computer Based Social Engineering
• Mobile Based Social Engineering
Social Sites Hacking And Protection
• Reality Behind Hacking Of Social Sites
• Advance phishing attack Facebook
• Stealing Saved Password Browser
• Hijack Of Facebook
Metasploit Framework- All in One Hacking Console
• Getting Started
• Component Metasploit
• Authentication Bruteforcing Against Online Services
• Metasploit Gui Armitage
• Armitage One More Step
• Msfvenom Create Trojan For Windows
• Client Side Attack Linux Trojan
Wireless Hacking- WPA-WPA2 Encryption
• Enable WEP WiFi Router
• Cracking Wirerless Encryption – WEP
• Enable WPA In Wifi Router
• Cracking Wifi WPA/ WPA2 Encryption
16 sections • 135+ lectures • 15+hour total length
. Introduction
. Understanding Linux
. What is Kali Linux
. What is Linux
. What is Linux Distro
. What are Desktops Enviroment
. Understanding Kernel
. What is Kernel
. Types Of Kernel
. Shell/Console
. What is Shell
. Installing Kali Linux
. Download Kali Linux (Updated 2023)
. Running Kali Linux Live
. Install Kali Linux on your PC
. Removing Kali Linux from your USB Pen Drive
. Understanding File Systems
. What is File System
. Most common File System
. FHS File System in Linux
. Understanding File in Linux
. File types in Kali Linux
. Kali Linux Directly Structure (Part 1)
. Kali Linux Directly Structure (Part 2)
. Important News
. Kali Linux Tools Sections
. Kali Linux Tool Section Explained
. Information Gathering Tools
. Vulnerability Analysis Tools
. Web Application Analysis Tools
. Database Assessment Tools
. Password Attack Tool
. Wireless Attacks Tools
. Reverse Engineering Tools
. Exploitation Tools
. Sniffing and Spoofing Tools
. Post Exploitation Tools
. Forensics Tools
. Reporting Tools
. Social Engineering Tools
. Using Terminal
. Kali Linux Terminal Basics
. Update Kali Linux through Terminal
. Creating File Through Terminal
. Making Directly Trough Terminal
. Deleting File in Terminal
. Packages & Terminal
. Installing Software Packages Through Terminal
. Copying File Through Terminal
. Moving File Through Terminal
. Renaming a File Through Terminal
. Head & Tail Command
. Changing IP Address Through Terminal
. Useful Kali Linux Commands
. Scripting Kali Linux
. Create Your First Script
. Final Lecture
. Congratulations
22 sections • 90+ lectures • 19hour total length
• Some Requirement
• System Requirement
• Download and Install VMware
• Download and Install Kali Linux
• how to Setup windows 10 in VMware
• What is Social Engineering
• What is Social Engineering-
• How Social Engineering works
• Social Engineering some other teachniq
• How to Install use and Run UserRecon Tool Kali Linux 2020
• What is Phishing
• What is phishing- Learn how this attack works – YouTube
• Setup Phishing Lab
• Abode
• Badoo
• Devianart
• Google
• Instafollowers
• Instagram
• Linkdin
• Netflix
• Pinterest
• Redroom
• All Phishing Pages
• Where You can buy Domain and hosting
• Which Domain you can buy
• Convert Phishing page to FUD
• Computer Hacking In social Engenerring
• How To Hack Computer Full Course – Ethical Hacking and Penetration Testing Tutorial 7
• How To Hack Computer Full Course – Ethical Hacking and Penetration Testing Tutorial 8
• How To Hack PC using Linux Ethical Hacking and Penetration Testing Tutorial 9
• how to hack thousend of computer t
• Mobile Hacking In social Engenerring
• Mobile Hacking In social Engenerring
• About MobiHuk Rat v4 by Sajawal Hacker
• How to hack android mobile in kali linux
• How to hack your friend phone camera without touching the phone
• Cloning Any Website and Harvesting User Passwords
• Phishing Page For linux Users
• Redirect your Victim to Milicious Website and Compromise his system,accounts and much more
• Sending Phishing link to gmail inbox
• Advanced IP Address Masking_ Hiding Your Real URL
• tools
13 sections • 50+ lectures • 8hour total length
• What is Virtualization
• What is Virtual Machine
• Kali Linux 2020
• Master Linux Commands
• Troubleshoot Kali Linux
• System Commands
• Network Commands
• User Commands
• Add and Delete User with full Sudo Permission
• What is DVWA
• What is XAMPP
• Command Injection Attack
• File Inclusion Attack
• File Upload Attack
• XSS Attack
• DOM Based XSS Attack
• Reflected XSS Attack
• Stored XSS Attack
• What is OWASP Mutillidae II
• Root Access
• SQL Injection
• SQL MAP
• How to solve Security Challenges
• Scan WebServer using NIKTO
• Burp Suite
• BEEF Framework
• OWASP Juice Shop
7 sections • 49+ lectures • 15+hour total length
• Practical Network Attacks
• Control connections of clients around you without knowing the password.
• Crack WEP/WPA/WPA2 using a number of methods.
• Hack any computer on the same network.
• Intercept data and spy on all on the network
• Gather detailed information about clients and networks like their OS, opened ports …etc.
• A number of practical attacks that can be used without knowing the key to the target network
• ARP Spoofing/ARP Poisonning
• Launch Various Man In The Middle attacks.
• Sniff packets from clients and analyse them to extract important info such as: passwords, cookies, urls, videos, images ..etc.
• Detect ARP poisoning and protect your self and your network against it.
• You will be able to use more than 20 penetration testing tools such as ettercap, wireshark, aircrack-ng suit …etc.
• Combine individual attacks to launch even more powerful attacks.
23 sections • 150+ lectures • 24+hour total length
• Kali Linux
• Parrot OS
• Ubuntu
• Termux
• Arch Linux
9 sections • 20+ lectures • 4hour total length
- How to hack open ports full course intro
- Hack Open Port 21tcp FTP server
- Hack open Port 22 SSH server
- Hack open Port 23tcp telnet server
- Hack open Port 25tcp smtp server
- Hack open Port 80tcp http server
- Hack open Port 111tcp rpc server
- Hack open Port 139,445tcp samba server
- Hack open Port 512,513.514tcp RSH server
- Hack open Port 1099tcp java-rmi server
- Hack open Port 1524tcp bindshell server
- Hack open Port 2049tcp nfs server
- Hack open Port 3306tcp mysql server
- Hack open Port 5432tcp postgresql server
- Hack open Port 5900tcp vnc server
- Hack open Port 6000tcp x11 server
- Hacking live website
8 sections • 20+ lectures • 5+hour total length
• Introduction to Hardware
• SMPS
• Hard Disk Drive
• Input-Output System
• Software
• Motherboard
• Printer
• Random Access Memory
• Mobile Device
• PC Assemble and Disassemble
• Processors
• Cables and Ports
• Diagnose and Resolve issues Related to PC
• What is Booting
• What is OS and Install Windows Server and CentOS
• Laptop
• Summary of Computer Hardware
19 sections • 19+ lectures • 7+hour total length
• What is Network
• Networking Devices
• Transmission Media
• What is LAN Basics
• Structured Cabling
• What is Topology
• OSI Model
• TCP IP Model
• Network Protocol
• IP Adressing
• Wireless Networking
• Network Troubleshooting
• Remote Access
• Working with Networked Devices
• File Sharing & Troubleshooting
• Network Threats & Mitigation
• Interview Questions
• Career Guideline
9 sections • 30+ lectures • 6+hour total length
• How To Crack windows Password
• How To By pass windows Password
• How to Make Your windows password uncrackable
• How to Hide Drives In windows
• Viruses
• Forward Port Free of Cost
• Forward Port By VPN
• Hacking on 127.0.0.1
• Pc Rat
• What is Worm
• Binding Virus with Files
• Keylogger Configuration
• Hack Computer With jpg, Mp3
• Hack Computer with Registry file
5 sections • 25+ lectures • 8+hour total length
• What is Malware
• What is Remote Access Trojan
• What is Port Forwarding
• How to Port Forward
• How to use a RAT for Hacking a System
• Port Forwarding Method 2
• How to use a RAT for Out of the Network
• What is Steganography
• How to To hide image or text file
• How to Hide Or Unhide Folders In windows
• How to Hide A message Into A song
18 sections • 90+ lectures • 12+hour total length
• Introduction To Start Hacking From Zero Level For Beginners
• Hacking Basic FAQ
• Different Types Of Hacking Attacks
• Basic Guide For Windows Users
• Useful Software’s and Browser Extensions for Windows Users
• What is IP Address and IP Address Types
• What is Port and Port Forwarding
• Install VMware and Virtual Box on Windows
• Install Windows on VMware or Virtual Box
• Install Kali Linux on VMware or Virtual Box
• Kali Linux Basics
• Fix Kali Linux Slow Package Downloading Problem
• Network Scanning Using Windows, Linux
• Setup Virtual Android Phone LAB For APK Testing
• Share Your Android Phone Screen To Windows, Linux, macOS
• Install JAVA JDK in Windows
• Metasploit Basics For Beginners
• Before Making Any Virus You Must Know These Things
• Hack Android Phone Using MSF
• Hack Windows Using MSF
• Hack Wi-Fi Password Using Kali Linux
• Social Media Accounts Password Hacking
• Android Phone Hacking Using RAT ( Remote Access Trojan )
• Windows Hacking Using RAT ( Remote Access Tool )
• Basic Reverse Engineering on Android Applications
• Basic Reverse Engineering on Windows Software’s
• Basic Malware Analysis Tutorial
• Learn Hacking Through an Android Phone Guide For Beginners
• How To Learn Hacking by Yourself Guide For Beginners
10 sections • 50+ lectures • 14+hour total length
• Introduction to Python
• Control Statements and Conditions in Python
• Collections in Python
• Python Functions
• File Handling in Python
• Exception Handling
• Object Oriented Programming
• Regular Expression
• Python Database Communications
• Python GUI Programming
• Course Summary
7 sections • 35+ lectures • 3+hour total length
• Introduction to Cloud Computing
• Cloud Computing Deployment Models
• Cloud Computing Service Models
• Advance Concepts in Cloud Computing
• Virtualization in Cloud Computing
• Interview Questions
• Career Guideline
20 sections • 100+ lectures • 15+hour total length
• Introduction
• What is JavaScript
• Setting Up the Development
• JavaScript in Browsers
• Separation of Concerns
• JavaScript in Node
• Variables
• Constants
• Primitive Types
• Dynamic Typing
• Objects
• Arrays
• Functions
• Types of Functions
• Operators
• Control Flow
• Objects
• Arrays
• Functions
18 sections • 110+ lectures • 17hour total length
• Introduction To Bug Bounty
• Information Gathering
• Setting Up Labs
• Introduction To Burf Suites
• SQL Injection
• Web Application Attacks
• Croos Site Scripts
• Header Injection & URL Redirection
• Client Side Attacks
• Brute Forcing
• Security Misconfiguration & Exploiting Web Apps
• Insecure CORS
• File Inclusion Vulnerability
• Server-Side Request Forgery
• Insecure Captcha
• Automation VAPT & Advance Information Gathering
• Documenting & Reporting Vulnerability
• Conclusion Of Bug Bount
• Introduction Training Plan
• What is Networking
• OSI Model & TCP IP Protocol Suite
• Types of Netowrk Device and Working
• Types of Network Security Devices and Working
• Bit, Hexadecimal & Bytes Represenation
• MAC Address & IP Address
• NAT
• PAT
• Basics of Wireshark & Tshark
• What is the Internet Layer & IP Header
• What are the IP Header Fields
• What is the Transport Layer & TCP Header
• What are the Transport Header Fields
• What are the common attacks performed with Transport Layer
• What is UDP Protcol & UDP Header
• What are the UDP Header Fields
• What is the ICMP Protocol & ICMP Header
• What are the ICMP Header Fields
• Common Attacks Performed with ICMP Protocol
• Protocols vs Ports
• What is ARP Protocol
• Client-Server Model
• What Is HTTP & How does it works
• What is DHCP & How does it works
• What is DNS & How does it works
• Basics of FTP, Telnet, SSH & SMTP
• DNS Zone Transfer Attack and Remediation
• Host Disovery Attcack and Remediation
• Port Scanning Attack and Remediation
• Vulnerabilty Scanning Attack and Remediation
• Arp Poisoning & MITM Attack and Remediation
• DOSDDOS Attack and Remediation
• Workgroup & Domain
• Cryptography
• Windows Password
• Windows Authentication
• Linux Basics
• Windows & Linux Logs
• System Exploitation
• Malware Types
• Brute Force Attack
• Brute Force Attack – Part 1 & Remediation
• Brute Force Attack – Part 2 & Remediation
• Privilege Escalation attack & Remediation
• Phishing Attack & Remediation
• Multiple Geo Location Access & Remediation
• Malware Detection & Remediation
• Zero Day Attack & Remediation
• Web Application Introduction
• Web Application Working
• Web Application Attack
• Poodle Attack
• Heart bleed Attack
• Shellshock Attack
• SQL Injection Attack & Remediation
• XSS Injection Attack & Remediation
• CSRF Injection Attack & Remediation
• Antivirus Working & Detection
• USECASE – Virus Outbreak
• Ransomware
• Conficker Worm
• Working, Detection & Evasion
• Working, Types and Reporting
• Attacking Phase 1 Reconnaissance
• Attacking Phase 2 Scanning
• Attacking Phase 3 Attacking
• Attacking Phase 4 Maintaining Access
• SIEM Installation
• Logs Forwarding to SIEM
• SIEM Hunting For Logs
• SIEM Dashboard Usage & Creation
9 sections • 50+ lectures • 6+hour total length
• Gain the advanced knowledge of Wi-Fi hacking from a professional Cyber Security Expert!
• Be able to break any type of Wi-Fi security (WEP/WPA/WPA2) & take full control of that network
• Master up-to-date methods and techniques.
• Be able to protect your own network from other malicious hackers.
• Master Wi-Fi hacking methods & become a Wi-Fi security specialist.
• Hack Wireless Networks (WEP, WPA, WPA2).
• Pentesting Using Raspberry PI, NODEMCU, Pineapple and Kali Linux
• Breaking WEP
• Breaking WPA/WPA2 (WPS Enabled)
• Breaking WPA/WPA2 (WPS Disabled)
• Breaking WEP on Windows
• Breaking All Types of WIFI-Encryptions
• Bypassing Extra Security Layers in a router
10 sections • 30+ lectures • 11+hour total length
Introduction
• Course Intro & Overview
Weaponizing
• Preparing Your Android Device
• Net Hunter Preview and Lab Overview
Installing Kali Linux As Virtual Machine
• Installing Kali E7 As a Virtual Machine
• Basic Overview of the operating system
Information Gathering
• Discovering Wireless Networks – Wardriving
• Preparing Your Device To Crack WiFi Keys_Passwords – WEP_WPA_WPA2
• Network Mapping – Discovering Devices Connected To The Network
• Network Mapping – Discovering Open Ports
• Network Mapping – Discovering Installed Services
Spying
Introduction
• MITM(Man in the Middle Attack)
Spying _ MITM Method 1 – Bad USB Attack
• What Is The Bad USB Attack & How To Launch It
• Sniffing Data & Capturing Passwords
• Bypassing HTTPS
• DNS Spoofing
Spying _ MITM Method 2 – ARP Poisoning
• What Is ARP Poisoning
• ARP Poisoning & Sniffing Data Using arpspoof
• ARP Poisoning & Sniffing Data Using Zanti2
• Intercepting Downloaded Files
• Replacing Images & Injecting Javascript Code
Spying _ MITM Method 3 – Fake Access Point (Honey Pot)
• Fake Access Point Theory
• Configuring Access Point Settings
• Launching The Fake Access Point
• Sniffing Data Sent Over The Access Point
Detection & Protection
• Detecting ARP Poisoning Attacks
• Detecting Suspicious Activity in the Network & Solutions to ARP Poisoning
Exploitation (Gaining Access)
• Introduction
• Bypassing Windows_OSX Logins – Setup
• Bypassing Windows_OSX Logins
• Creating An Undetectable Backdoor
• Using Metasploit Meterpreter
• Replacing Downloads With A Backdoor
• Backdooring Downloads On The Fly
• HID Keyboard Attack- Executing Windows Commands On Target Computer Via USB
• HID Keyboard Attack – Gaining Full Control Over Windows Machine
Exploitation – Rubber Ducky Scripts
• What Are Rubber Ducky Scripts & How To Use Them
• Automatic Download & Execute To Gain Full Control Over Windows
• Reverse OSX Shell To Gain Full Control Over Mac OSX Computers
• Reverse Linux Shell To Gain Full Control Over Linux Computers
Detecting Malicious Files
• Protecting Yourself Against Backdoor Delivery Methods
• Detecting Undetectable Backdoors
9 sections • 40+ lectures • 12+hour total length
- Understanding MITM Attacks
- Types of MITM Attacks
- Exploiting Network Vulnerabilities
- ARP Spoofing and DNS Spoofing
- SSL Stripping and HTTPS Bypassing
- Packet Sniffing and Session Hijacking
- Wireless MITM Attacks
- MITM Attack Tools and Techniques
- Countermeasures and Mitigation Strategies
- Real-World Case Studies and Examples
- Legal and Ethical Implications in Cybersecurity
10 sections • 55+ lectures • 11+hour total length
• Cyber Forensics Investigations
• Search and Seizure of Digital Evidence and first Responder Responsibilities
• Computer Forensics
• Mobile Forensics
• Email Forensics And Analysis
• Fundamental of OSINT
• Network Forensics
• Course Summary
• Project
• Career Guideline
9 sections • 40+ lectures • 4+hour total length
- How To Instal l& Setup Apk Easy Tool In Windows
- How To Make Fud Botnet Apk Bypass All Mobile Security
- How To Make Fud Botnet 2 Apk Bypass All Mobile Security
- How To Make Fud Rat Apk
- How To Make Fud Rat 2 Apk
- How To Make Fud Rat Apk Bypass All Mobile Security
- How To Make Fud Rat Apk 2 Bypass All Mobile Security
- How To Make Long Time Fud Apk
- Fud Mobihok Apk
11 sections • 20+ lectures • 4+hour total length
• How To Setup A Android KeyLogger
• How TO Make Anti-UnInstall With Coding
• How TO Make Anti-Reset Payload With Coding
• How to make Payload Anti-ADB With Coding
• How to make Anti-Power Off Payload With Coding
• How to Bind Anti-UnInstall Payload Other Rat
• How to make Anti-UnInstall Third Party Apk
• Anti-Uninstall+Bind Third Party Apk
• Make Anti-UnInstall Payload Malware Bind
• Make Persistent Payload Part1
• Make Persistent Payload Part2
2 sections • 10+ lectures • 2+hour total length
• Difference between dark web and deep web
• How To Get Darkweb Links
• How To access dark web without tor
• dark web & deepnet search engines
• How to make your own tor website
8 sections • 16+ lectures • 6+hour total length
• Introduction
• How to Successfully Instal Python and its Modules
• How to get 1000+ Website List
• How to get Shell, SMTP , Admin Panel Login and Much More
• Deep Video For many Bots
• All Checkers
• How to Get 10000+ Websites List
• Spamming And Phishing
• Most Important Topic
10 sections • 25+ lectures • 13+hour total length
• Introduction to OSINT: Fundamentals and Overview
• Sources of Open-Source Intelligence
• Advanced Search Techniques and Operators
• Social Media Intelligence (SOCMINT)
• Geolocation and Image Analysis
• Dark Web and Deep Web Exploration
• OSINT Tools and Software Overview
• Data Collection and Analysis Methods
• Ethical and Legal Considerations in OSINT
• Practical Exercises and Case Studies
• Reporting and Presenting OSINT Findings
• OSINT Automation and Workflow Strategies
• OSINT for Threat Intelligence and Detection
• Digital Forensics and Information Verification
9 sections • 50+ lectures • 8+hour total length
• Introduction to Advance JAVA
• MVC
• Servlet
• Web APP Listener
• Session Management
• Java Server Pages
• JSTL and EL
• Servlet Filter
• Java Mail API
15 sections • 50+ lectures • 11+hour total length
• Introduction
• Run Mobile on Windows
• Install Kali Linux on Mobile Phone
• Run iPhone on MAC
• Hack Android with Metasploit
• L3MON Framework
• Android Debug Bridge
• Android Mirroring
• OWASP GOAT
• Ghost Framework
• Hacking from Phone
• Android Hack via Browser Attacks
• Remotely Manage Computer From Android
• Mobile Phone Defense
11 sections • 50+ lectures • 9+hour total length
• Introduction
• PHP With OOPS
• Features of OOPS
• Email Handling
• Introduction to MVP Architecture
• CRUD Operations using MVC Architecture
• Introduction to APIs and Web Services
• Payment Gateway
• PHP and AJAX
• Web Services and AJAX CRUD Operations
• Interview Questions
11 sections • 70+ lectures • 9+hour total length
. Intorduction
. Definations
. TCP-IP Model Physical&Data Link (Network Access) Layer
. TCP-IP Model Internet (Network) Layer
. TCP-IP Model Transport Layer
. TCP-IP Model Transport Layer TCP
. TCP Attack Vector #1
. TCP Attack Vector #1 Response Challenges
. TCP Attack Vector #2
. TCP Attack Vector #3 and Combinations
. TCP Attack Vector #4
. TCP Attack Vector #5
. TCP-IP Model Transport Layer UDP
. UDP Attack Vector #1
. TCP-IP Model Application Layer
. Overview
. TCP-IP Model Application Layer Web
. Web Attack Vector #1
. Web Attack Vector #1 Response Challenges
. Web Attack Vector #2
. TCP-IP Model Application Layer DNS
. DNS Attack Vector #1
. DNS Attack Vector #2
. TCP-IP Model Application Layer Remaining Protocols
. Attack Vector #1-4
. Attack Vector #5
. Protection & Mitigation
. Overview
. Proper Firewall Configuration
. Rate Controls
. Proper Load Balancer and Router Configuration
. Protection with CDNs
. What is a CDN
. Does CDN protect you against DDoS
. Important Things to Consider Deploying a CDN Solution
. Conclusion
Top Companies Hiring Ethical Hackers in Pakistan

What Our Students Are Saying!
We are proud to have positively influenced the career foundations for thousands of learners across Pakistan and Asian countries.












Meet Your Cybersecurity Guru

Hello, I’m Salman . With over a decade of experience in the cybersecurity field, I’ve had the privilege of working across various sectors, from government agencies to private corporations. My passion for cybersecurity led me to teaching, where I aim to share not just theoretical knowledge but the practical insights I’ve gained through hands-on experience. My approach to teaching is all about making complex concepts easy to understand. I’m here to guide you through real-world scenarios and equip you with the skills needed to excel in this ever-evolving industry. Together, we’ll navigate the intricacies of cybersecurity, empowering you to build a solid foundation and excel in your journey towards becoming a skilled cybersecurity professional
FAQ
Our cybersecurity course is designed to accommodate learners with various backgrounds. While some technical familiarity can be helpful, we offer comprehensive content suitable for beginners and those looking to enhance their existing skills.
For the majority of the course, you’ll only need a standard computer with internet access. Specific software requirements will be outlined in the course materials. We aim to keep the tools and resources accessible.
Yes, our course content is crafted to align with industry standards and best practices. Completing our course provides valuable knowledge and skills that are relevant in the cybersecurity field.
Absolutely! We encourage interaction. You’ll have opportunities to ask questions, participate in discussions, and collaborate with instructors and fellow students. We believe that learning is most effective when it’s a shared experience.
The course duration varies depending on your pace and commitment. On average, students complete the course in 6 Months, but you’re free to learn at your own speed. We provide lifetime access to the course materials, allowing you to revisit and review as needed.
Yes, you will have continued access to the course materials even after completion. We believe in the importance of ongoing learning, and you can refer back to the content to reinforce your knowledge or stay updated on the latest cybersecurity developments.
Buy Now!
